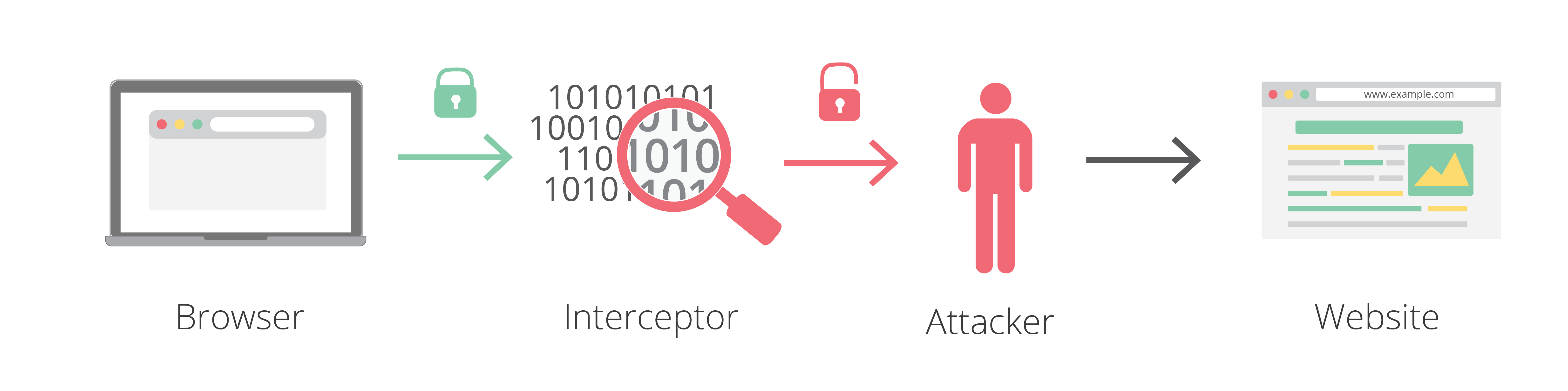
HTTP is the most common internet protocol. Most of the things we do online are implemented on HTTP, from the usual web browsing to instant messaging. Unfortunately, HTTP communications are unprotected and relatively easy to intercept, making them a prime target for MITM attacks. As mentioned earlier, hackers can sit between end users and the website they’re connected to and eavesdrop on their communications, including any information they submit to the website, without them having any idea.
How Do You Prevent HTTP Interception?
SSL/TLS Certificates
If your website still uses the more vulnerable HTTP protocol, it’s time to upgrade to the safer HTTPS protocol through SSL/TLS Certificates. A TLS Certificate will activate the HTTPS protocol, which is the safer version of HTTP. This allows an encrypted, secure connection between your server and your clients’ computers, keeping all information from prying hackers.
TLS Certificates can also bind together your domain name and your organizational identity if you get an Organization Validated (OV) or Extended Validation (EV) level certificate. EV Certificates bring your identity information front and center by displaying your organization name right in the URL bar. This can boost trust among your visitors that your site is legitimately operated by your company and not an imposter site.
System and Server Configurations
Don’t sit on your laurels just yet. Once TLS is up and running, you need to do some configuring. Make sure your website doesn’t have any mixed content or any page element loading over an HTTP protocol (e.g. photos, scripts, widgets) to avoid leaving a backdoor for aspiring hackers. It’s also good practice to make sure any links you are pulling in from other sites are via HTTPS. Make sure your login forms are HTTPS-protected to avoid credential hijacking. Mozilla is already doing a great job preventing users from filling up forms under HTTP protocols by “unsecure connection” warning prompts and a slashed padlock icon. Make sure all hyperlinks contained in your website all use the HTTPS protocol.
It’s also important to make sure you have your server configured correctly (e.g. using the current best practices for protocols, algorithms, etc.). For example, you should make sure you have SSL2, SSL3, and TLS1 protocols disabled; only TLS 1.1 and 1.2 should be enabled. There are many other configuration items to consider and recommended best practices are continually changing as new vulnerabilities are discovered. GlobalSign’s SSL Server Test is an easy-to-use and thorough tool for making sure your server is properly configured


No comments:
Post a Comment