As an infosec professional, you’ve likely heard about using a cyber kill chain, also known as a cyber attack lifecycle, to help identify and prevent intrusions. Attackers are evolving their methods, which might require that you look at the cyber kill chain differently. What follows is a recap of what the cyber kill chain approach to security is and how you might employ it in today’s threat environment.
What is a cyber kill chain?
In military parlance, a "kill chain" is a phase-based model to describe the stages of an attack, which also helps inform ways to prevent such attacks. These stages are referred to as:
- Find
- Fix
- Track
- Target
- Engage
- Assess
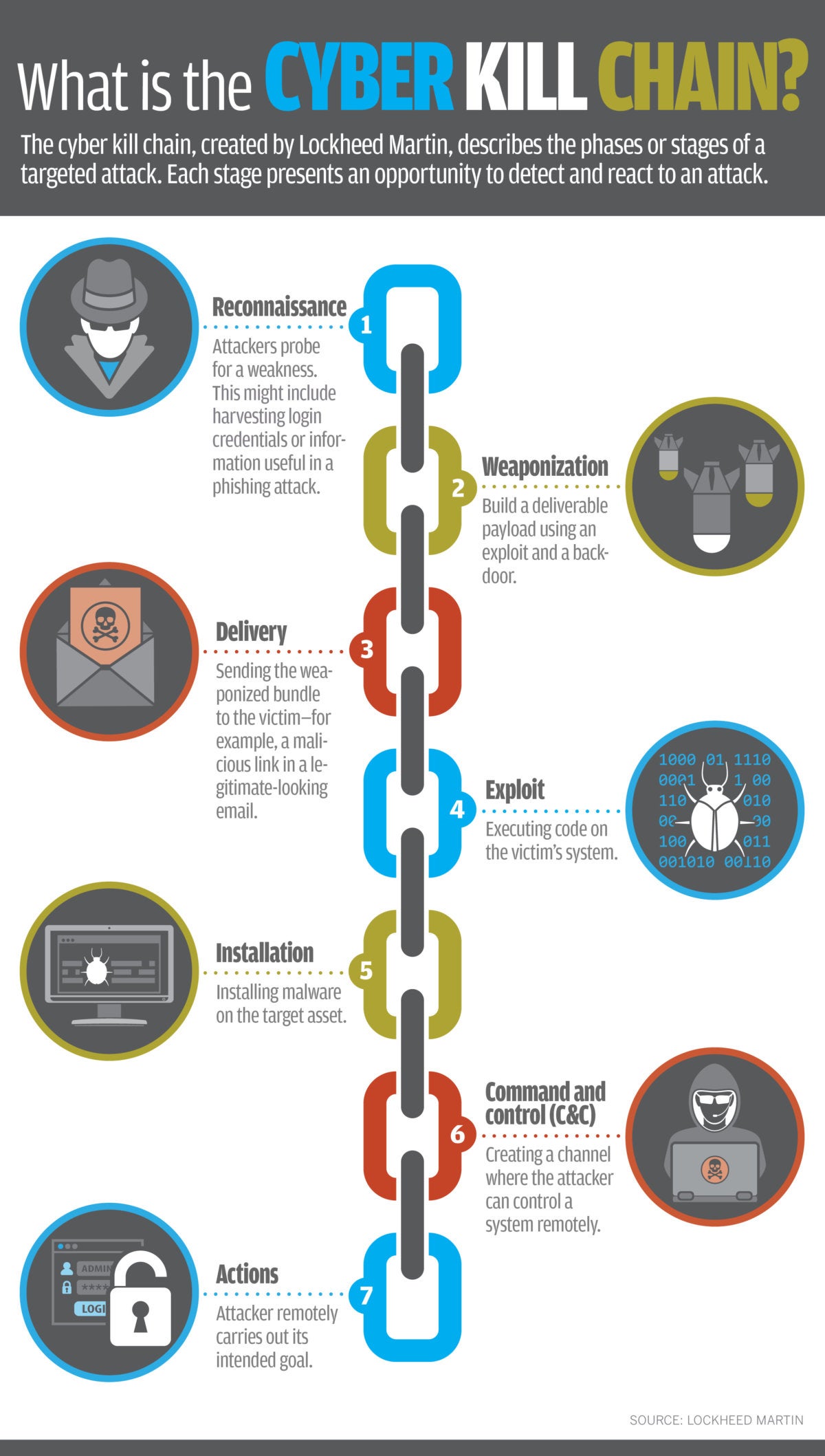
The cyber kill chain is a similar idea, which was put forth by Lockheed Martin, where the phases of a targeted attack are described. Likewise, they can be used for protection of an organization's network. The stages are shown in the graphic below.
It's a lot like a stereotypical burglary. The thief will perform reconnaissance on a building before trying to infiltrate it, and then go through several more steps before actually making off with the loot. Using the cyber kill chain to keep attackers from stealthily entering your network requires quite a bit of intelligence and visibility into what's happening in your network. You need to know when something is there that shouldn't be, so you can set the alarms to thwart the attack.
Another thing to keep in mind is the closer to the beginning of the chain you can stop an attack, the less costly and time-consuming the cleanup will be. If you don't stop the attack until it's already in your network, you'll have to fix those machines and do a whole lot of forensics work to find out what information they've made off with.
Let's look at the various stages to determine what questions you should be asking yourself to decide whether it's feasible for your organization.
Reconnaissance: Viewing your network from the outside
At this stage, criminals are trying to decide what are (and are not) good targets. From the outside, they learn what they can about your resources and your network to determine whether it is worth the effort. Ideally, they want a target that is relatively unguarded and with valuable data. What information the criminals can find about your company, and how it might be used, could surprise you.
Companies often have more information available than they realize. Are names and contact details of your employees online? (Are you sure? Think social networks too, not just your own corporate website.) These could be used for social engineering purposes, say, for getting people to divulge usernames or passwords. Are there details about your web servers or physical locations online? These could be used for social engineering too, or to narrow down a list of possible exploits that would be useful to break into your environment.
This is a tricky layer to control, particularly with the popularity of social networking. Hiding sensitive information tends to be a fairly inexpensive change, though being thorough about finding the information can be time-intensive.
Weaponization, delivery, exploit, installation: Attempting to enter
These stages are where the criminals craft a tool to attack their chosen target, using the information they have gathered, and putting it to malicious use. The more information they can use, the more compelling a social engineering attack can be. They could use spear-phishing to gain access to internal corporate resources with the information they found on your employee's LinkedIn page. Or they could put a remote access Trojan into a file that appears to have crucial information on an upcoming event in order to entice its recipient into running it. If they know what software your users or servers run, including OS version and type, they can increase the likelihood of being able to exploit and install something within your network.
These layers of defense are where your standard security wonk advice comes in. Is your software up to date? (All of it, on every machine. Most companies have that one box in some back room that is still running Windows 98. If it's ever connected to the Internet, it's like having a welcome mat outside your door.)
Do you use email and web filtering? Email filtering can be a good way to stop common document types that are used in attacks. If you require that files be sent in a standard way, such as in a password-protected ZIP archive, this can help your users know when files are being sent intentionally. Web filtering can help keep users from going to known bad sites or domains.
Have you disabled autoplay for USB devices? Giving files the chance to run without approval is seldom a good idea from a security perspective. It's better to give the user a chance to stop and think about what they're seeing before it launches. Do you use endpoint protection software with up-to-date functionality? While endpoint protection software is not intended to deal with brand-new targeted attacks, sometimes they can catch threats based on known suspicious behavior or known software exploits.
Command and control (C&C): The threat is checking in
Once a threat is in your network, its next task will be to phone home and await instructions. This may be to download additional components, but more likely it will be contacting a botmaster in a C&C channel. Either way, this requires network traffic, which means there is only one question to ask yourself here: Do you have a firewall that is set to alert on all new programs contacting the network?
If the threat has gotten this far, it's made changes to the machine and is going to require a lot more work from IT staff. Some companies or industries require that forensics be done on the affected machines to determine what data has been stolen or tampered with. Those affected machines will either need to be cleaned or reimaged. It can be less costly and time-consuming if the data has been backed up and there is a standard corporate image that can be quickly replaced onto the machine.
Some attacks follow their own rules
As this past year has amply demonstrated, attackers aren't following the playbook. They skip steps. They add steps. They backtrack. Some of the most devastating recent attacks bypass the defenses that security teams have carefully built up over the years because they're following a different game plan. "The kill chain as invented by Lockheed Martin is malware focused, and that makes certain attacks invisible," said Alton Kizziah, VP of global managed services at Kudelski Security.
"[The cyber kill chain has] never been a clean fit for the attacks we've seen," said Misha Govshteyn, cofounder and SVP of products and marketing at Alert Logic, Inc., which primarily monitors data center security.
This year, web applications attacks where the most common type of data breach, according to this year's Verizon Data Breach Investigations Report, accounting for nearly a third of all breaches. One common approach is to take advantage of a vulnerability in the application itself.
The recent Equifax breach was just the latest high-profile example. It can be hard to spot this kind of attack. Equifax didn't spot suspicious network traffic on its website for more than two months. "It’s often only at the point of exfiltration that an organization will realize they have a compromise," said Leigh-Anne Galloway, cybersecurity resilience lead at Positive Technologies. "Or it might take a third-party entity, such as a customer, to alert the company to the issue."
The Equifax breach was traced back to a vulnerability in the Apache Struts web server software. If the company had installed the security patch for this vulnerability it could have avoided the problem, but sometimes the software update itself is compromised, as was the case in September with Avast's CCleaner software update.
Then there are the zero-day exploits. According to Jeff Williams, CTO and cofounder at Contrast Security, software applications and APIs average 26.8 serious flaws per app. "That’s a staggering number," he said. "The public was outraged at the negligence of Equifax, but the fact is that almost every company is equally insecure at their application layer. We are seeing widespread application attacks probing from thousands of IP addresses all over the world."
To protect against these kinds of attacks, companies need to speed up their patch deployment. "It used to be that attacks would take weeks or months to emerge after an application vulnerability was disclosed," he said. "Today, that safe window has been reduced to about a day, and will probably be only a few hours in 2018."
Companies also need to start embedding security controls directly into applications themselves, he said. It's called runtime application self protection, and Gartner predicts a 9 percent compound annual growth rate for this market segment.
"Security needs to move closer to the application, and go deeper into core processes and memory usage," said Satya Gupta, founder and CTO at Virsec Systems, Inc. "New control flow technology, embedded at the application level, understands application protocols and context, and can map the acceptable flow of an application--similar to a Google map. If the application is supposed to go from point A to point B, but makes an unexpected detour, then something is definitely wrong."
Attackers can also use a compromised credential or take advantage of weak, default or nonexistent passwords. No malware needs to be installed, there's no communications with a C&C server, and no lateral movement. "Finding a leaked database or an Amazon S3 bucket means the attack is accomplished without much that the defenders can do," said Ben Johnson, CTO at Obsidian Security, Inc.
According to a report released this month by RedLock, 53 percent of organizations that use cloud storage services like Amazon S3 have accidentally exposed at least one such service to the public. Earlier this summer, Skyhigh Networks reported that 7 percent of all AWS S3 buckets used by enterprises have unrestricted access, and 35 percent are not encrypted.
Since the data is leaving through a legitimate channel, the exfiltration defenses might not pick it up, either. "You need specialized tools to protect specifically against web application attacks," said Govshteyn.
Or take a denial of service attack. "You still have to pick your target, so there is some reconnaissance," said Sam Curry, CSO at Cybereason, Inc. After that, the attackers jump straight to the disruption phase.
A denial of service attack could also be just the first step, he added, helping to mask other malicious behavior. "When you stress a system, you can create a vulnerability," he said. "Or you create a high signal-to-noise ratio, flood the defenders to drown the evidence and destroy the ability to find the signal."
Attackers can also add steps to their game plan, he said. For example, they can take time to clean up traces of their presence, set up disruptions, spread false data, or install backdoors that they can use for future attacks.
They can also do the steps out of order, or go back and repeat steps. It's not a simple linear process, he said. "It's usually more like the spreading branches of a tree," he said. "Or spreading tentacles, with lots of things happening."
Monetizing the attack: It ain't over till it's over
In the denial of service example, disruption isn't necessarily the last step of an attack. Once they've successfully disrupted, corrupted or exfiltrated, attackers can go back in and do it all over again.
Or they can move on to another stage -- monetization. According to Ajit Sancheti, CEO at Preempt Security, that can take any number of forms. For example, they can use compromised infrastructure to commit ad fraud or send out spam, extort the company for ransom, sell the data they've acquired on the black market, or even rent out hijacked infrastructure to other criminals. "The monetization of attacks has increased dramatically," he said.
The use of Bitcoins makes it easier and safer for the attackers to receive money, he added, which contributes to the change in the motivation behind attacks. The number of different groups involved in the consumption of stolen data has also become more complicated. That could, potentially, create opportunities for enterprise to work with law enforcement authorities and other groups to disrupt the process.
Take, for example, stolen payment card information. "Once credit card data is stolen, the numbers have to be tested, sold, used to procure goods or services, those good or services in turn have to sold to convert them to cash," said Monzy Merza, head of security research at Splunk, Inc.


No comments:
Post a Comment