The rapid advances in digital technology over the past several decades have also brought to the fore new challenges around data privacy and security. As a result, hacks, identity theft and other digital violations of privacy are becoming commonplace.
These issues have been thrown into sharp focus courtesy of the recent Cambridge Analytica controversy and the European Union’s General Data Protection Regulation (GDPR). Addressing the challenge of how to secure the internet has been a primary motivation for many of us in the Blockchain community for a much longer time, however. As Blockchain technology re-architects our digital infrastructure, it also reformulates the security equation.
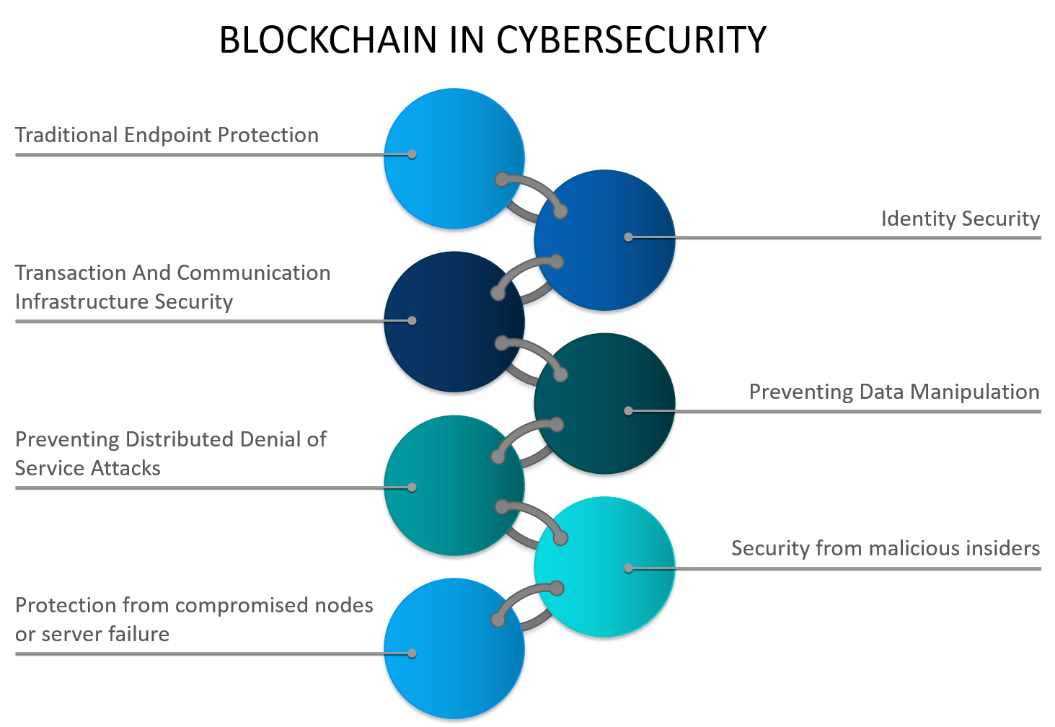
A simple take on Blockchain is that it can be applied to any activity that requires a database, and it follows that Blockchain software brings to bear tools that tackle data management issues, particularly around security, privacy and authentication.
One of distributed ledger technology’s most fundamental attributes is that it makes data immutable. Once a log is made of an action or transaction, it cannot be altered or falsified. This offers a whole new level of transparency, and consequently security.
Furthermore, network administrators never have access to users’ passwords, meaning there is no gateway for them to control or manipulate users’ data. Instead, thanks to use of private key authentication, they receive only a snapshot of the identities of individual users.
A matter of access
Newer Blockchain platforms have taken this principle one step further by providing extremely robust systems of permissions to allow different degrees of access to the network. These permissions are customizable and can be governed by atomic actions, which are indivisible sequences of primitive operations that must be enacted without interruption.
Newer Blockchain platforms have taken this principle one step further by providing extremely robust systems of permissions to allow different degrees of access to the network. These permissions are customizable and can be governed by atomic actions, which are indivisible sequences of primitive operations that must be enacted without interruption.
On applications built on EOSIO, Blockchain software protocol developed by Block.one, participants have different degrees of access. In logistics management, for example, one type of key could allow access only for data entry, another for monitoring data entry, and a third for administering transfers of tokens between accounts. This keeps different activities, and access to data, segmented.
This stratified system of permissions, which didn’t exist in older public Blockchain platforms, offers enterprises a way of regulating who can do what and thereby minimizing security wormholes for hackers to exploit.
Turning users into stakeholders
At a time when internet users want more control over the data they provide (and which they generate as they go about their digital lives), the ability of Blockchain to stop third parties from accessing data for marketing and advertising purposes is an attractive proposition for many people.
At a time when internet users want more control over the data they provide (and which they generate as they go about their digital lives), the ability of Blockchain to stop third parties from accessing data for marketing and advertising purposes is an attractive proposition for many people.
Blockchain enables new models where users become participants. When you transmit data, or transact in such an ecosystem, you are rewarded with tokens. With a stake in the game, your role becomes active rather than passive. We are already seeing token-based applications where users play the part of activist stakeholders.
This can have a huge impact on the management, production and delivery of goods and services, and on how organizations handle data from everyone who interacts with their network.
Meeting the security challenge
In-keeping with its goal of achieving mass adoption of Blockchain technology, Block.one has been fully engaged in exploring how Blockchain can improve the relationship between technology and users’ privacy and security.
At the company’s recent EOS Global Hackathon series event in London, participants were asked to consider the ways in which the technology can put data back in the hands of users and come up with solutions that deliver on this promise.
In-keeping with its goal of achieving mass adoption of Blockchain technology, Block.one has been fully engaged in exploring how Blockchain can improve the relationship between technology and users’ privacy and security.
At the company’s recent EOS Global Hackathon series event in London, participants were asked to consider the ways in which the technology can put data back in the hands of users and come up with solutions that deliver on this promise.
Winning projects included a device that prevents smart contracts from interacting with blacklisted actors, a “smart” bank account, an app that simplifies credit-checking by taking it out of the hands of third-party providers, and another that incentivizes individuals to donate genomics data in a secure, anonymized way.
As these ideas illustrate, a world bolstered by Blockchain technology heralds a re-engineered digital landscape in which security and transparency are integral. In the short to medium term, leaks, cyber-attacks and mismanagement of data are likely to intensify, making it all the more urgent that privacy and security issues are addressed.
As these ideas illustrate, a world bolstered by Blockchain technology heralds a re-engineered digital landscape in which security and transparency are integral. In the short to medium term, leaks, cyber-attacks and mismanagement of data are likely to intensify, making it all the more urgent that privacy and security issues are addressed.


No comments:
Post a Comment